From the past few months, researchers have observed a new malware campaign that is scanning Docker servers on the internet running exposed API misconfigured open ports that has no password in it that installs a crypto mining malware named ‘ Kinsing’ in them.
The campaign is running from months in the wild with thousands of attempts were taking place on a daily basis said Aqua researchers.

Since the main purpose of the malware is to mine cryptocurrency on the compromised docker but it also downloads and installs a version of ClamAV antivirus that usually detects other local malware running on the docker port and removing it, but it also runs a script that gathers local SSH credentials to infect other cloud systems with other malware.
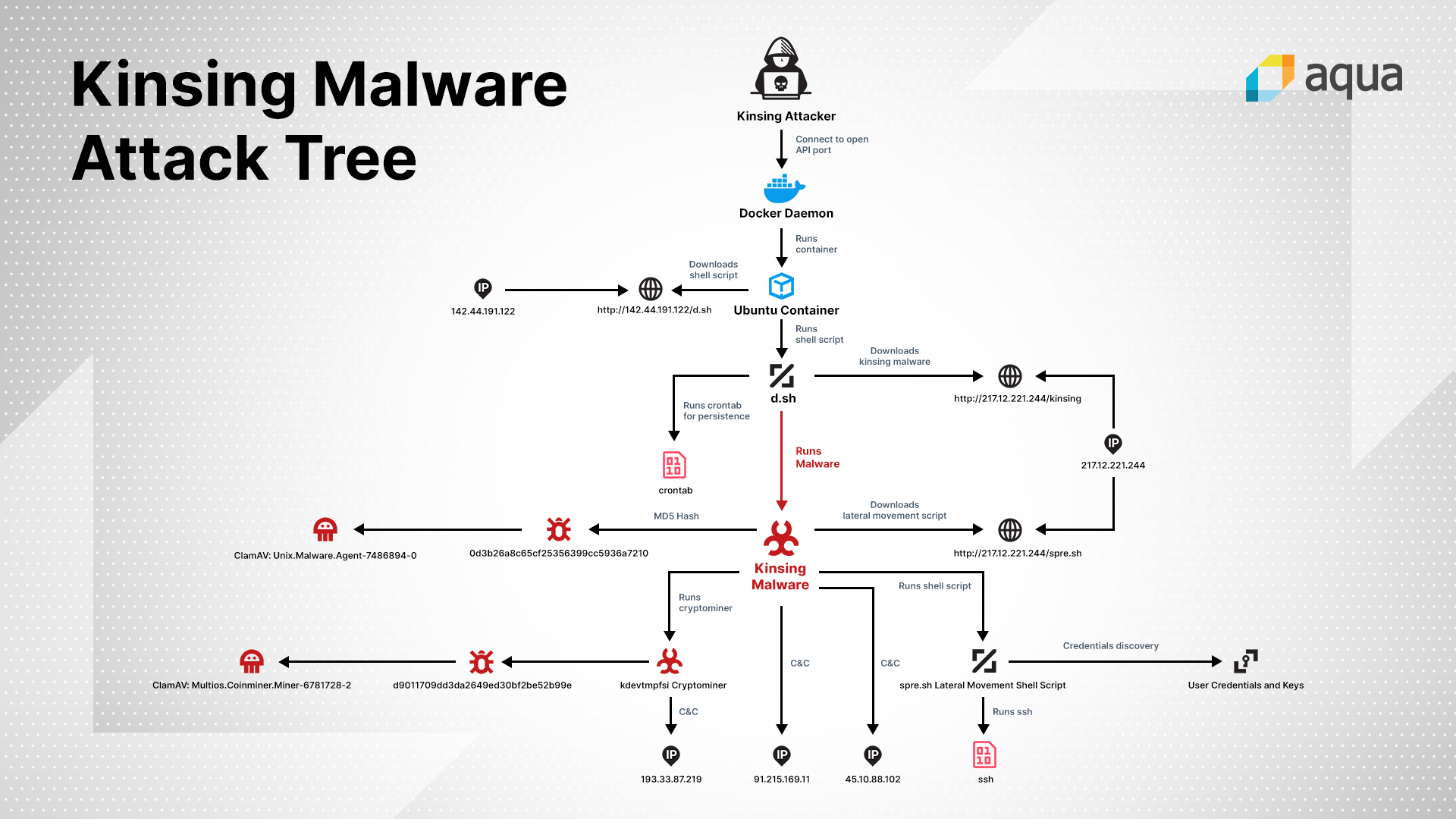
How kinsing malware is initiated
The attackers are taking advantage of the unprotected Docker ports through which they are able to instantiate an ubuntu container. After the entry, the attackers download a shell script d.sh that contains more than 600 lines of code and does the following:
- Clearing logs and disabling security measures
- Kills other malware and crypto miners running
- Remove other malware from the docker
- Downloading the Kinsing malware
Kinsing is a Linux agent and written in Go lang. Before execution of the payload, the malware communicates with the C&C server that is located in Eastern Europe. The malware connects over HTTP port 80 and sends small encrypted messages on a regular interval of time.
Such attacks started since 2018 and Aqua and Sysdig were the first two companies to identify these type of docker based attacks.
MD5s:
kinsing – 0d3b26a8c65cf25356399cc5936a7210
kinsing – 6bffa50350be7234071814181277ae79
kinsing – c4be7a3abc9f180d997dbb93937926ad
kdevtmpfsi – d9011709dd3da2649ed30bf2be52b99e





