According to researchers Fortigate VPN default, config can push organizations towards the man-in-the-middle (MitM) attacks through which threat actors can intercept important data of the organizations.
According to SAM IoT Security Lab, the FortiGate SSL-VPN client only verifies that the certificate that used for client authentication was issued by Fortinet or another trusted certificate authority.
Therefore the attacker can easily present a certificate issued to a different Fortigate router without raising any flags and hence can implement a man-in-the-middle attack.
On further research, the researchers found that over 230,000 vulnerable Fortigate appliances and over 200,000 businesses are using default configuration that is vulnerable to MITM attacks.
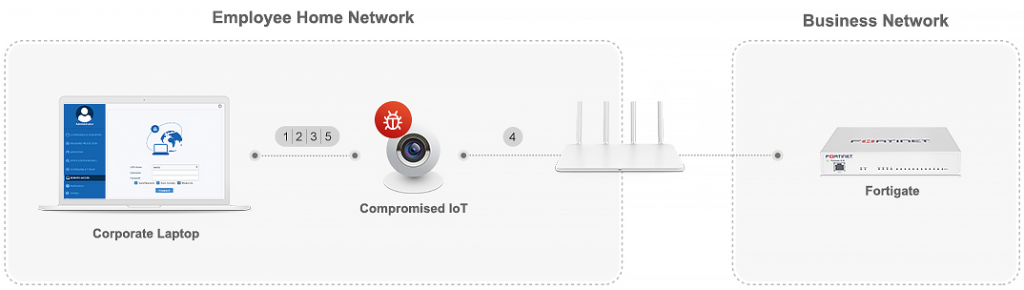
An attacker can use this to inject his traffic and essentially communicate with any internal device in the business, including point of sales, sensitive data centres, etc. This is a major security breach, that can lead to severe data exposure
Researchers said
Technical Detail of Fortigate VPN Issue
During an SSL certificate verification, the server checks if the certificate issue to the same server the client is trying to connect to or the certificate validity date has not passed if all the processes are verified the client is considered as a valid user.
But the Fortigate certificate validation had major issues that the Fortigate router comes with a default SSL certificate that is signed by Fortinet (Self-signed, that is, it was not issued by a trusted CA). Each Fortigate has its certificate that uses the router’s serial number as the server name for the certificate. However, the Fortigate’s client does not verify the Server Name at all.
Proof of Concept is also published by SAM showing how attackers can easily intercept the username and passwords.
Fixing the Issue
However, Fortigate doesn’t consider this as a vulnerability because the user can manually replace the certificate, it is the user’s responsibility to make sure the connection is protected.
However, according to us, we didn’t find the answer reasonable because smaller businesses may not have the knowledge or they don’t know the process. Also, there is no clear warning by Fortinet to the user.
Users are recommended to change the Fortigate VPN default, config to be safe such attacks.




